Modern digital systems increasingly rely on automated identity verification. From unlocking smartphones to managing secure facilities, facial recognition software has become a foundational technology for recognizing individuals accurately and efficiently. This article explores how face recognition software functions, where it is applied, and why organizations rely on face recognition programs for scalable identity verification.
What Facial Recognition Software Is
Facial recognition software is a biometric technology that identifies or verifies a person by analyzing facial features from images or video streams. Unlike traditional authentication methods such as passwords or ID cards, it relies on biological characteristics, making identity verification faster and more secure.
Face recognition software converts facial characteristics into mathematical representations, which are compared against stored records to find a match. These systems are widely used in security, authentication, and analytics-driven applications.
How Facial Recognition Software Works
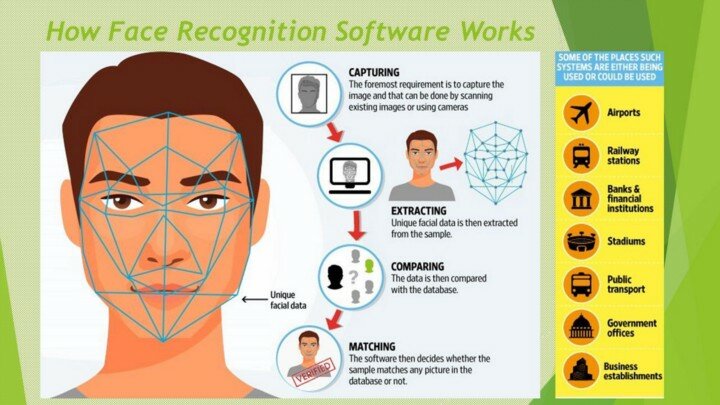
A typical face recognition program follows a structured workflow:
- Capture an image or video frame
- Detect faces within the image
- Extract distinctive facial features
- Convert features into numerical embeddings
- Compare embeddings with stored templates
This process enables facial recognition software to operate in real time, even in large-scale deployments.
Core Components of a Face Recognition Program
A complete face recognition program includes several technical components:
- Image acquisition module
- Face detection engine
- Feature extraction model
- Matching and decision system
- Database management layer
Each component must work together to ensure accuracy and reliability.
Face Detection vs Face Recognition
Face detection identifies the presence of a human face in an image, while face recognition determines whose face it is. Facial recognition software relies on detection as a prerequisite step. Without accurate detection, recognition performance degrades significantly.
Algorithms Used in Face Recognition Software
Modern facial recognition software uses deep learning models, particularly convolutional neural networks. Common algorithmic approaches include:
- Eigenfaces and Fisherfaces
- Local Binary Patterns
- Deep neural embeddings
- Siamese neural networks
These methods allow face recognition programs to learn complex facial patterns.
Data Collection and Preprocessing
High-quality data is essential for face recognition software. Preprocessing steps include:
- Face alignment
- Noise reduction
- Lighting normalization
- Image resizing
These steps improve consistency and recognition accuracy.
Training Models for Face Recognition Programs
Training a face recognition program requires large datasets of labeled facial images. Models learn to distinguish subtle differences between faces while remaining robust to variations such as aging, lighting, and expressions.
Accuracy Metrics and Evaluation
Performance evaluation of facial recognition software involves metrics such as:
- Precision
- Recall
- False acceptance rate
- False rejection rate
These metrics help assess reliability in real-world scenarios.
Real-Time Face Recognition Software in Practice
Real-time facial recognition software processes video streams to identify individuals instantly. This capability is crucial for surveillance systems, access control, and smart city applications.
Industry Applications
Facial recognition software is deployed across multiple sectors:
- Security and surveillance
- Consumer electronics
- Banking and payments
- Healthcare systems
- Retail analytics
Each sector benefits from automated identity verification.
Facial Recognition Software in Security Systems
Security-focused facial recognition software enhances access control by replacing physical keys and cards. It reduces unauthorized entry risks and enables seamless authentication.
Face Recognition Software in Smartphones and Consumer Devices
Smartphones use face recognition software for device unlocking, app authentication, and secure payments. These systems balance speed, usability, and privacy.
Use in Banking and Financial Services
Banks use facial recognition software for customer onboarding, fraud prevention, and secure transactions. Face recognition programs streamline compliance with identity verification regulations.
Healthcare and Patient Identification
Hospitals use facial recognition software to identify patients accurately, reducing medical errors and improving service efficiency.
Retail and Customer Analytics
Retailers use face recognition programs to analyze customer demographics, track store visits, and personalize experiences while respecting data protection laws.
Government and Public Sector Use
Governments deploy facial recognition software for border control, law enforcement, and national ID systems. These applications require strict governance and transparency.
Ethical Considerations and Privacy Concerns
The adoption of facial recognition software raises ethical questions related to surveillance, consent, and data security. Responsible deployment requires clear policies and safeguards.
Bias and Fairness in Face Recognition Programs
Bias in training data can affect recognition accuracy across demographics. Developers must ensure face recognition programs are trained on diverse datasets to minimize unfair outcomes.
Legal and Regulatory Landscape
Different regions regulate facial recognition software differently. Compliance with data protection laws such as GDPR is essential for lawful operation.
Facial Recognition Software in Edge Computing Environments
With the rise of edge computing, facial recognition software is increasingly deployed closer to data sources rather than centralized servers.
This approach:
- Reduces latency in real-time recognition
- Improves data privacy by limiting data transmission
- Enables offline face recognition programs
Edge-based systems are commonly used in surveillance cameras, smart kiosks, and industrial access systems.
Role of Computer Vision in Face Recognition Software
Computer vision provides the foundational techniques that enable face recognition software to interpret visual information.
Key computer vision tasks involved include:
- Image segmentation
- Facial landmark detection
- Pose estimation
- Feature normalization
Without these processes, reliable face recognition programs would not be possible.
Facial Feature Embeddings and Vector Space Representation
Modern face recognition software does not store images directly for comparison.
Instead:
- Facial images are converted into numerical vectors
- Vectors represent unique facial characteristics
- Similarity is measured using distance metrics
This vector-based approach enables scalable identity matching across millions of records.
Impact of Image Quality on Face Recognition Programs
The effectiveness of a face recognition program is strongly influenced by input quality.
Factors that affect performance:
- Camera resolution
- Motion blur
- Facial occlusion
- Environmental lighting
Improving image quality often delivers better results than changing algorithms.
Cross-Age and Cross-Environment Recognition Challenges
One of the most complex problems in facial recognition software is recognizing individuals across time and environments.
Challenges include:
- Aging effects
- Changes in hairstyle or facial hair
- Use of accessories
- Environmental variations
Advanced training techniques help models generalize across these variations.
Facial Recognition Software in Access Control Systems
In enterprise environments, facial recognition software replaces traditional access methods.

Benefits include:
- Touchless authentication
- Reduced credential theft
- Faster identity verification
These systems are widely used in offices, airports, and restricted facilities.
Use of Face Recognition Software in Education
Educational institutions deploy face recognition programs for:
- Attendance tracking
- Campus security
- Examination identity verification
Such implementations require transparency and consent mechanisms.
Facial Recognition Software in Smart Cities
Smart city infrastructure increasingly integrates face recognition software for public safety and traffic management.
Applications include:
- Crowd monitoring
- Missing person identification
- Restricted zone enforcement
Governance frameworks are critical for ethical deployment.
Privacy-Preserving Face Recognition Techniques
To address privacy concerns, researchers are developing techniques such as:
- Federated learning
- Encrypted facial embeddings
- On-device recognition
These approaches limit exposure of personal biometric data.
Dataset Diversity and Model Generalization
The accuracy of facial recognition software depends heavily on training data diversity.
Balanced datasets help:
- Reduce demographic bias
- Improve fairness
- Enhance global applicability
Dataset governance is as important as algorithm design.
Facial Recognition Software and Deepfake Detection
Face recognition programs are increasingly integrated with deepfake detection systems.
This helps:
- Identify synthetic identities
- Prevent impersonation attacks
- Strengthen digital trust systems
As synthetic media grows, this integration becomes essential.
Performance Optimization Techniques
To improve efficiency, face recognition software uses:
- Model compression
- Quantization
- Hardware acceleration
These techniques enable deployment on low-power devices.
Security Risks and Threat Models
While powerful, facial recognition software introduces security risks.
Common threats include:
- Spoofing attacks
- Adversarial inputs
- Dataset poisoning
Mitigation strategies include liveness detection and continuous monitoring.
Interoperability with Identity Management Systems
Enterprise face recognition programs often integrate with:
- IAM platforms
- Access management tools
- Authentication services
This enables centralized identity governance.
Measuring Business Impact of Face Recognition Software
Organizations assess impact through:
- Reduced fraud rates
- Faster onboarding times
- Improved operational efficiency
Quantifying outcomes strengthens adoption justification.
System Architecture of Facial Recognition Software
Enterprise facial recognition software is built as a modular system to support scalability and reliability.
A typical architecture includes:
- Input acquisition layer for cameras or image sources
- Preprocessing and normalization services
- Face detection and alignment modules
- Feature extraction and embedding generation
- Matching engine and decision logic
- Storage and identity management systems
This separation allows independent upgrades and better fault tolerance.
Cloud-Based vs On-Premise Face Recognition Programs
Organizations choose deployment models based on security, cost, and latency.
Cloud-based systems
- Easier to scale
- Centralized updates
- Higher network dependency
On-premise systems
- Greater data control
- Lower latency
- Higher infrastructure cost
Hybrid models are increasingly common.
Continuous Learning in Face Recognition Software
Modern face recognition programs support continuous learning.
This enables:
- Adapting to new facial data
- Handling gradual appearance changes
- Improving accuracy over time
Controlled retraining prevents performance degradation.
Facial Recognition Software Model Drift Detection
Over time, recognition accuracy may decline due to environmental or population changes.
Drift detection involves:
- Monitoring similarity score distributions
- Tracking false acceptance rates
- Identifying sudden accuracy drops
Early detection prevents system failure.
Face Recognition Software in Low-Light Conditions
Low-light environments pose significant challenges.
Solutions include:
- Infrared imaging
- Noise-resistant feature extraction
- Specialized training datasets
These techniques improve reliability in night-time scenarios.
Facial Recognition Software and Liveness Detection
Liveness detection ensures that the face being analyzed belongs to a real person.
Common techniques include:
- Eye blink detection
- Depth sensing
- Texture analysis
- Motion consistency checks
This protects systems from spoofing attacks.
Handling Large-Scale Databases Efficiently
As databases grow, matching speed becomes critical.
Optimizations include:
- Approximate nearest neighbor search
- Vector indexing
- Hierarchical clustering
These methods enable real-time recognition at scale.
Explainability in Face Recognition Programs
Explainability helps stakeholders understand system decisions.
Explainable features:
- Similarity score breakdowns
- Confidence thresholds
- Match reasoning logs
This improves transparency and trust.
Audit Trails and Logging
Enterprise facial recognition software maintains detailed logs.
Logs track:
- Recognition attempts
- Access decisions
- System errors
- Model updates
Audit trails support compliance and forensic analysis.
Facial Recognition Software in Workforce Management
Organizations use face recognition programs to:
- Track employee attendance
- Manage shift access
- Prevent time fraud
Such systems must comply with labor laws.
Integration with Video Management Systems
Face recognition software often integrates with VMS platforms.
This enables:
- Real-time alerts
- Historical video analysis
- Centralized monitoring
Integration simplifies operational workflows.
Facial Recognition Software Performance Benchmarks
Benchmarking ensures system quality.
Common benchmarks evaluate:
- Recognition accuracy
- Latency
- Scalability
- Resource utilization
Regular benchmarking maintains performance standards.
Dataset Annotation and Quality Control
Accurate labeling is critical.
Best practices include:
- Multi-reviewer validation
- Annotation consistency checks
- Continuous dataset audits
Quality data improves model reliability.
Cultural and Social Acceptance Factors
Public acceptance influences deployment success.
Factors affecting acceptance:
- Transparency of usage
- Perceived benefit
- Trust in institutions
Social context matters as much as technology.
Facial Recognition Software in Border Control
Border security systems rely on high-accuracy recognition.
These systems:
- Verify traveler identity
- Detect imposters
- Speed up immigration processes
Strict oversight is essential.
Cost Considerations and ROI Analysis
Organizations evaluate:
- Infrastructure costs
- Licensing fees
- Maintenance expenses
- Operational savings
Clear ROI justifies long-term adoption.
Interdisciplinary Collaboration in Development
Successful face recognition software requires collaboration between:
- Computer vision engineers
- Data scientists
- Security experts
- Legal advisors
- Ethics committees
This ensures balanced system design.
Responsible Decommissioning of Face Recognition Systems
When systems are retired:
- Data must be securely deleted
- Access credentials revoked
- Audit records archived
Responsible decommissioning protects user privacy.
Strategic Roadmap for Long-Term Deployment
Organizations should plan:
- Periodic audits
- Model upgrades
- Policy reviews
- Stakeholder communication
Strategic planning ensures sustainable use.
Advantages of Facial Recognition Software
Key benefits include:
- Contactless authentication
- High scalability
- Improved security
- Faster verification processes
These advantages drive widespread adoption.
Limitations and Technical Challenges
Despite advancements, facial recognition software faces challenges such as:
- Sensitivity to lighting
- Occlusion issues
- Aging effects
- Data privacy risks
Continuous research addresses these limitations.
Comparison with Other Biometric Systems
Compared to fingerprints and iris scans, facial recognition software offers convenience but may require stronger safeguards for accuracy and privacy.
Future Trends in Face Recognition Software
Emerging trends include:
- Edge-based recognition
- Privacy-preserving models
- Multimodal biometric systems
These innovations aim to enhance trust and performance.
Best Practices for Implementation
Organizations implementing facial recognition software should:
- Conduct privacy impact assessments
- Ensure data security
- Maintain transparency
- Regularly audit model performance
Following best practices ensures ethical and effective use.
Conclusion
Facial recognition software has transformed identity verification by offering scalable, efficient, and intelligent solutions. As face recognition programs continue to evolve, balancing technological innovation with ethical responsibility remains essential for sustainable adoption.
FAQ’s
How secure are facial recognition systems?
Facial recognition systems can be highly secure when combined with liveness detection, encryption, and strong data governance, but their effectiveness depends on implementation quality and protection against spoofing and bias.
How to build a facial recognition software?
Facial recognition software is built by collecting face images, preprocessing and detecting faces, extracting features using deep learning models, and matching them against a trained database for identification or verification.
Which technology is used in the face recognition system?
Face recognition systems use computer vision and deep learning technologies, especially convolutional neural networks (CNNs), to detect faces, extract features, and match identities accurately.
How does facial recognition software work?
Facial recognition software works by detecting a face, extracting unique facial features using AI models, and comparing them with stored templates to identify or verify a person.
What are the different types of facial recognition?
The main types of facial recognition include 2D facial recognition, 3D facial recognition, thermal facial recognition, and skin texture analysis, each using different methods to identify and verify faces.



